Which of the Following Is Used for Biometric Authentication
Thus the biometric data remains secure as long as the device itself is not compromised. All of the following are used for authentication except.
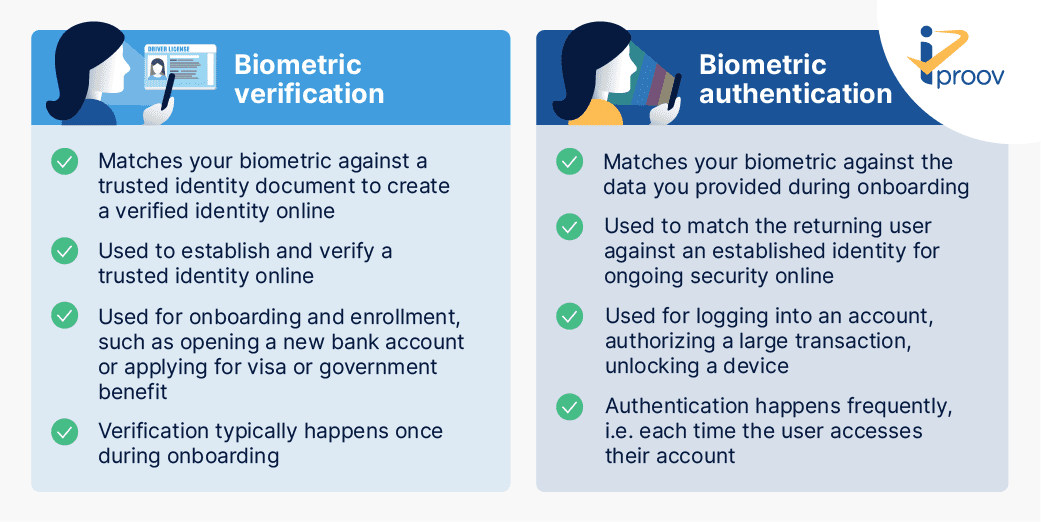
Biometric Authentication Vs Biometric Verification Iproov
Match each of the following terms to its meaningIpacket filteringIIIP addressIIIfirewallIVCAPTCHAVbiometric authentication deviceAprogram that generates distorted text and requires that it be typed into a boxBreads a unique personal characteristic and converts its pattern to a digital codeChardware or software for protecting computers from.

. With biometric authentication the risk of a bad actor gaining access to user systems and information decreases when used as part of a multi-factor authentication strategy. The convenience factor is high. Biometric identification uses biometrics such as fingerprints or retina scans to identify a person whereas biometric authentication is the use of.
Which of the following is not included in the term biometric information as described by the Aadhaar Targeted Delivery of Financial and Other Subsi. Security of the physical hardware used throughout the biometric data life cycle. Biometric authentication can now be found in almost every phone.
If both samples of the biometric data match authentication is confirmed. Biometric authentication is a security process that relies on the unique biological characteristics of individuals to verify they are who they say they are. Encapsulation of biometric data Security of the physical hardware used throughout the biometric data life cycle Techniques for integrity and privacy protection of biometric data.
What is biometric input. So I have used d instead. The following references were used to develop the Biometric Authentication knowledge-base article.
Typically biometric authentication is used to manage access to physical and digital resources such as buildings secure areas and computing devices. Many areas such as passport verification airports buildings mobile phones identity cards 9. Which of the following are examples of biometric authentication methods currently used.
Digital signatures O certificates of authority. Information Technology B facial features. Benefits of using biometric authentication.
A smart cards B facial features C passwords D personal identification numbers Answer. Why Biometric Authentication Is Bad. A biometrics template or identifier a sample known to be from the authorized user must be stored in a database for the device to compare.
The following highlights benefits precautions and strategies for protecting data subjects and biometric data. Which of the following is used for biometric authentication. A smart card has a microprocessor and integrated circuits used to process data whereas a memory card has a magnetic strip that.
Gait Signature Voice Recognition and Facial Recognition are physiological biometric that could be used for authentication. Benefits of biometric authentication. Biometric authentication systems compare physical or behavioral traits to stored confirmed authentic data in a database.
28 Which of the following is used for biometric authentication. User acceptance and usability is also better than anything else in the market. The following were incorrect answers.
Asked Feb 27 in GK by Aniketk 300k points. Fingerprint Retinal scan Blood sampling Voice recognition Rectal Scan Facial recognition Soit identication Question. Biometrics that can utilize something that you hold in your hand dozens of times a day either because of Pokémon or WhatsApp is a very handy device to use in authentication.
Biometrics authentication devices rely on physical characteristics such as a fingerprint facial patterns or iris or retinal patterns to verify user identity. Instead of typing a password we can just authenticate by tap the fingerprint. Which of the following is used for biometric authentication.
In this article well look into how to implement Fingerprint Authentication in flutter apps. Biometric authentication is when the users fingerprints facial patterns and voice are used to verify their identity. Which of the following are examples of biometric authentication methods currently used.
Biometrics authentication is becoming popular for many purposes including network logon. Facial features A ________ pretends to be a legitimate company and sends an email requesting confidential data such as account numbers Social Security numbers account passwords and so forth. Encapsulation of biometric data.
Biometrics recognition systems are used in are based on a single source of modality. It is authentication 16Biometrics systems are used to secure therefore necessary to move beyond biometric systems that medical records. You havent specified what Y is here.
All other choices presented were incorrectly describing identification and authentication mapping. Many devices today use biometric input for authentication. Write a C program to read two strings then find the length of these strings and use the division A.
The consideration of references does not. Typically smartphones use on-device storage of biometric templates which ensures authentication occurs without any data being sent to a server. Biometric has been for long the target of future authentication that expected that biometric authentication will largely displace other means of our current authentication and access control.
Usage of biometric technology including one-to-one and one-to-many matching for identification and authentication. Application of biometric technology for internal and external as well as logical and physical access control. In a typical office biometric authentication might be used to control access to employees and registered visitors only.
E All the options. We know the system will have some false negatives some employees falsely denied access so we need a human override someone who can examine the employee and allow access in spite of the failed authentication. Typically biometric authentication is.
Which of the following best describes the difference between memory and smart cards. Answered Apr 2 by sharadyadav1986. Here Is the code in C as follows.
Fingerprints facial recognition hand geometry iris recognition retinal identification voice recognition keystroke dynamics and handwritten signature. If both samples of the biometric data match authentication is confirmed. A memory card has a microprocessor and integrated circuits used to process data whereas a smart card has a magnetic strip that is used to hold information.
There are good reasons biometric authentication has expanded so rapidly.
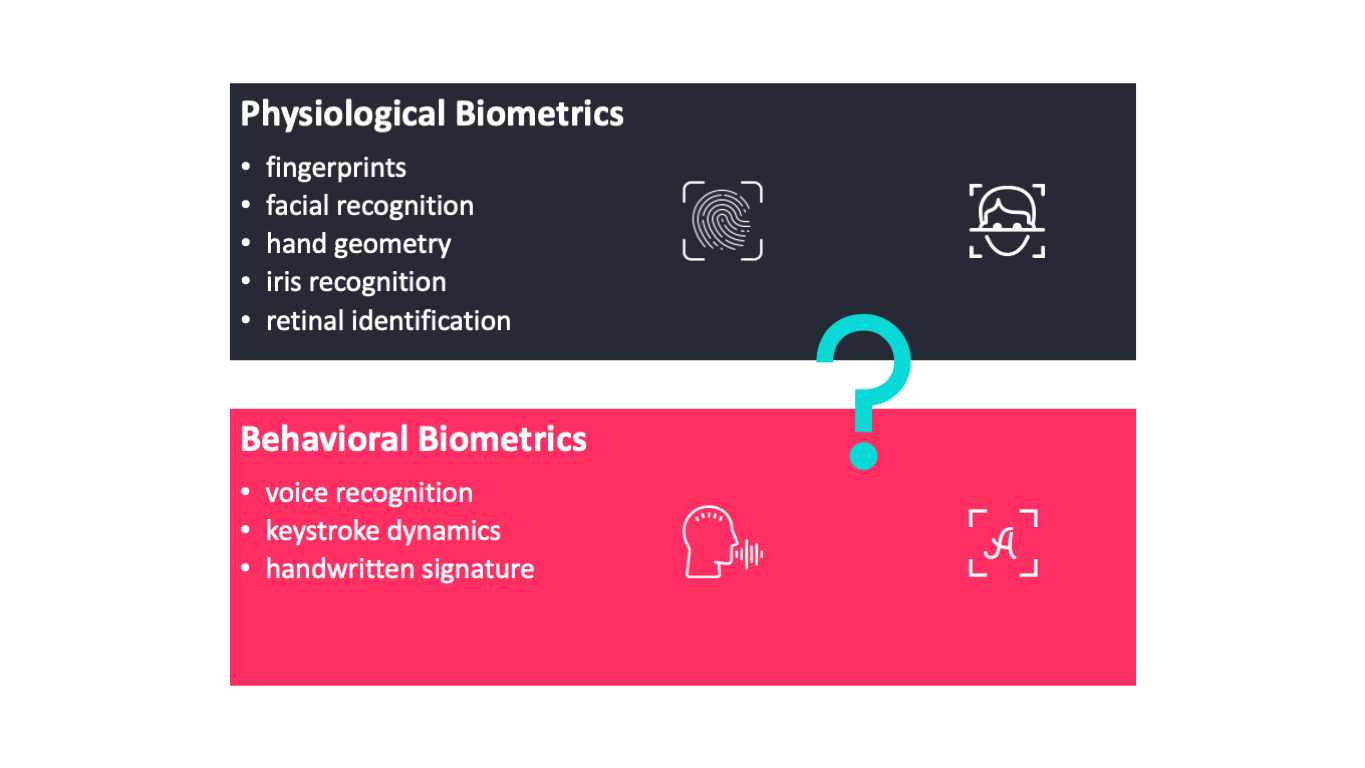
Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science

What Is Biometrics Authentication Types Of Biometrics And Trends

What Is Biometric Authentication Definition Benefits And Tools Toolbox It Security
Comments
Post a Comment